Petya 修改電腦 MBR 致無法進入 Windows
PETYA Crypto-ransomware Overwrites MBR to Lock Users Out of Their Computers
Trendmicro 2016-03-31 10:00:00http://blog.trendmicro.com/trendlabs-security-intelligence/petya-crypto-ransomware-overwrites-mbr-lock-users-computers/
PETYA Crypto-ransomware Overwrites MBR to Lock Users Out of Their Computers
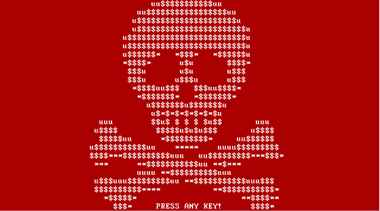
As if encrypting files and holding them hostage is not enough, cybercriminals who create and spread crypto-ransomware are now resorting to causing blue screen of death (BSoD) and putting their ransom notes at system startup—as in, even before the operating system loads. Imagine turning on your computer and instead of the usual Windows icon loading, you get a flashing red and white screen with a skull-and-crossbones instead.
This is the routine of a new crypto-ransomware variant dubbed “Petya” (detected by Trend Micro as RANSOM_PETYA.A). Not only does this malware have the ability to overwrite the affected system’s master boot record (MBR) in order to lock users out, it is also interesting to note that it is delivered to victims via a legitimate cloud storage service (in this case, via Dropbox).
We do note that this isn’t the first time that malware has abused a legitimate service for its own gain; however, this is the first time (in a long time) that leads to crypto-ransomware infection. It is also a departure from the typical infection chain, wherein the malicious files are attached to emails or hosted in malicious sites and delivered by exploit kits.
Infection Routine
Reportedly, Petya is still distributed via email. Victims would receive an email tailored to look and read like a business-related missive from an “applicant” seeking a position in a company. It would present users with a hyperlink to a Dropbox storage location, which supposedly would let the user download said applicant’s curriculum vitae (CV).
In one of the samples we analyzed, the Dropbox folder the link points contains two files: a self-extracting executable file, which purports to be the CV, and the applicant’s photo. Further digging revealed that the photo is a stock image that is most likely used without permission from the photographer.
Of course, the file downloaded isn’t actually a resume at all, but rather a self-extracting executable file which would then unleash a Trojan onto the system. The Trojan then blinds any antivirus programs installed before downloading (and executing) the Petya ransomware.
Infection Symptoms
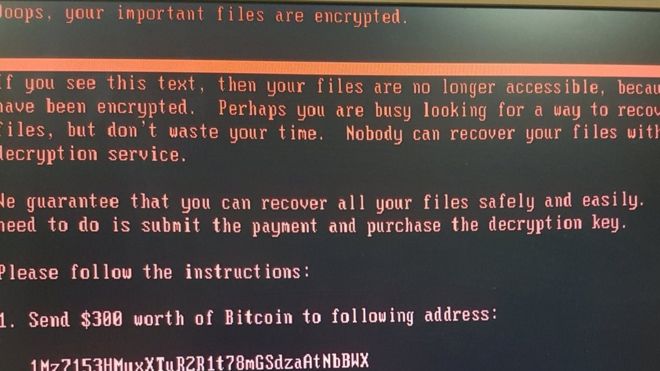
Once executed, Petya overwrites the MBR of the entire hard drive, causing Windows to crash and display a blue screen. Should the user try to reboot his PC, the modified MBR will prevent him from loading Windows normally and instead greet him with an ASCII skull and an ultimatum: pay up with a certain amount of bitcoins or lose access to your files and computer.
Another thing to point out here is that the edited MBR also disallows restarting in Safe Mode.
The user is then given explicit instructions on how to do this, just like any crypto-ransomware currently making the rounds: a list of demands, a link to the Tor Project and how to get to the payment page using it, and a personal decryption code.
Looking at its very professionally-designed Tor website, we discover that its ransom price is currently at 0.99 Bitcoins (BTC), or US$431 – and that said price would be doubled if the on-screen deadline for payment is missed. Trend Micro endpoint solutions such as Trend Micro™ Security, Smart Protection Suites, and Worry-Free™ Business Security can protect users and businesses from this threat by detecting malicious files, and email messages as well as blocking all related malicious URLs.